https://www.hackster.io/electronic-cats/can-flipper-hack-a-car-ce7ec0
CAN Flipper hack a car?
Dives you into using a Flipper Zero paired with CAN bus Add-On to access and interact with a car's CAN network. By Carlos Alatorre, Jazmín Hernández, and Andres Sabas.
www.hackster.io
Story
Electronic Cats Flipper CANBus Add-On 🐬
CAN bus Add-On is a board that allows Flipper Zero devices to connect to CAN bus networks. Along with the app, the Add-On can read real-time information through OBD2 connectors, making it useful for auditing cars.
Additionally, the app can communicate with “raw” CAN bus networks for sniffing and injecting messages. The app allows filtering the CAN dump, injecting messages to specific PIDs, and retrieving more information.
So let's begin, here is a video to warm up, showing one of the features of the Add-On, reading OBD2 data:
The primary aim of this tutorial is to expose the potential vulnerabilities of the CAN network in modern vehicles—not to bypass security features or gain unauthorized access, but to demonstrate how accessible data and commands are over this unencrypted network. By connecting the Flipper Zero device along with an Electronic Cats CANBus Add-On, either to a car’s OBD2 port or the CAN network, we’ll show how easy it can be to retrieve critical information and interact with vehicle systems in real-time.
We aim to emphasize the importance of cybersecurity in automotive design and encourage ethical research.
Understanding Car Electronics 🚘
Modern cars are built with intricate networks of Electronic Control Units (ECUs) that control and monitor nearly every electronic function. These ECUs act as miniature computers, each assigned to manage specific tasks: controlling engine performance, braking systems, transmission functions, and even comfort settings like air conditioning. The ECUs communicate with one another over a Controller Area Network (CAN), a robust protocol that enables them to exchange critical data and commands in real-time, ensuring the car operates as a cohesive system.

While the CAN protocol is efficient and reliable, it was not designed with robust security in mind. Once an unauthorized device gains access to the CAN network, it’s possible to read and, in some cases, inject CAN messages directly into the network. These messages, if crafted correctly, can control certain functions within the vehicle—from honking the horn to manipulating vehicle speed or locking systems.
Though auto manufacturers have implemented some safeguards, CAN networks remain susceptible to potential exploitation.
OBD2
The On-Board Diagnostics 2 (OBD2) port is a standardized gateway designed for vehicle diagnostics. OBD2 has become a versatile entry point to access real-time information on various vehicle parameters, read diagnostic codes, and even conduct performance tuning.

PID (Parameters IDs)
PID codes are used to request data from a vehicle. There is an expected response for each PID given. Not all vehicles will support all PIDs and there can be manufacturer-defined custom PIDs that are not defined in the OBD2 standard. For example, mode 0x01 contains standardized PIDs that provide real-time data on speed, RPM, and fuel level.
You can find more information about the available PID codes and how they work in OBD2 PIDs.
DTC Codes
DTC (Diagnostic Trouble Codes), also referred to as engine fault codes, are used to identify and diagnose malfunctions in a vehicle. When a vehicle’s OBD system detects a problem, it activates the corresponding trouble code.

Manufacturer-specific codes must be referred to official brand documentation.
Installing the App ⬇️
The app is compatible with any firmware for Flipper, official or custom, as long as it matches the firmware version to what the app was compiled to. There is not much to worry about in this aspect because the app is usually updated each time a new official firmware stable version is released, so you can use the app with any Flipper firmware you want.
To install it, you only need to:
1. Go to the app repository in the Things used for this project.
2. Go to the releases section or enter this link directly: Flipper CANBUS app releases.

3. Download the .fap file from the Assets section.

4. Connect your Flipper to either qFlipper,Flipper Lab or the Flipper mobile app (if Experimental Options are enabled).
5. Using the File Manager system, navigate to the Apps Folder.
6. Upload the .fap file to the path you prefer. It is recommended to create a new folder or use an existing folder as the “Misc” folder.
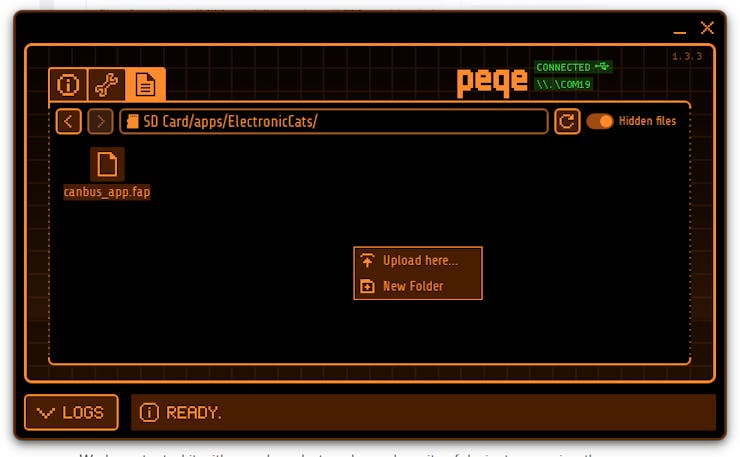
Done! When the app is installed, navigate in your Flipper to the path where the app file was saved and open it.
Find more information about the app and the Add-On in its wiki.
Testing with a real car
We have tested it with a real car, but we have done it safely, just accessing the OBD2 port and not connecting to the ECUs network. Connecting to the ECU network can break your car and can be dangerous for you and others, please act safely.
As shown in the video in the first section of this tutorial, we have been able to get typical data like the engine speed (RPM), time elapsed since the engine was turned on, and so on. Also, we have been able to get the VIN (Vehicle Identification Number), and DTC codes stored in the main ECU and delete them. Getting DTC codes along with your user manual book can be useful to get a better idea of what is going wrong with your car.
Here are some snapshots from the video:

This process was done by connecting the Flipper Add-On through an OBD2 connector, which only enables the CAN bus lines on the car's OBD2 port.
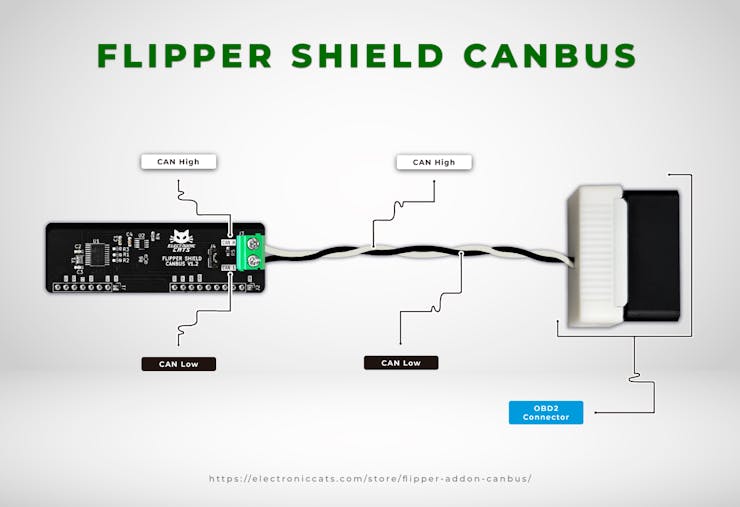
Testing with RAMN 🐏
RAMN (Resistant Automotive Miniature Network) is a miniature CAN/CAN-FD testbed of four Electronic Control Units (ECUs) that allows us to experiment without resorting to a real vehicle, which we could damage by playing with the CAN message injection.
Requirements:
- Flipper Zero with CANBUS Add-On.
- RAMN (built and programmed).
- Cables for connecting CAN High and CAN Low.
- Flipper MCP2515 CANBUS app installed on your Flipper.
Steps:
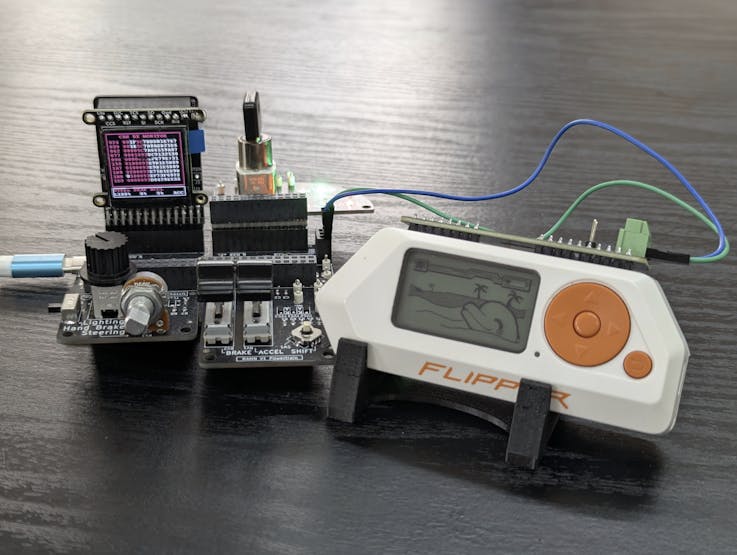
- Attach the CAN bus Module to the Flipper Zero. Ensure the CAN bus Add-on module is securely attached to your Flipper. This module enables the Flipper to connect to and communicate over a CAN network.
- Connect to the RAMN Simulator. Locate the CAN High and CAN Low terminals on the RAMN simulator.
- Locate the CAN High and CAN Low terminals on the RAMN simulator.
- Connect CAN High on the Flipper Add-On to CAN High on the RAMN.
- Connect CAN Low on the Flipper Add-On to CAN Low on the RAMN.
- Go to the CAN dump section in RAMN.
- Open the CAN bus app in the Flipper.
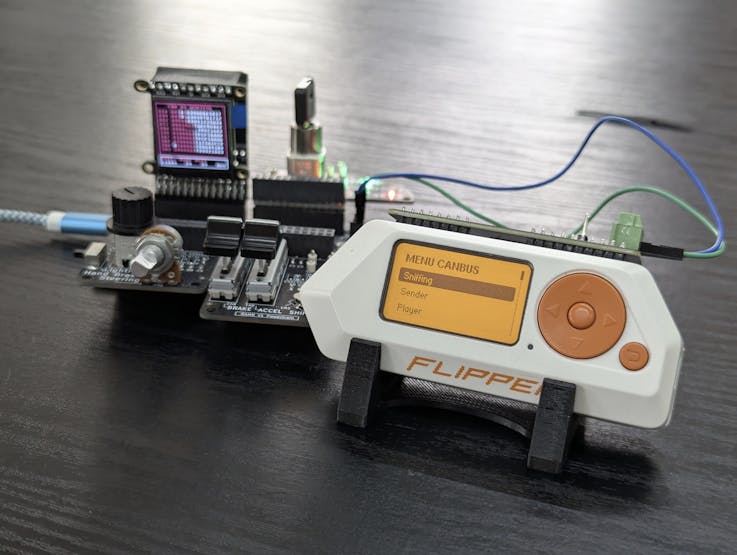
Now, it is possible to sniff the CAN dump, inject packets, and read OBD2 data. RAMN does not support OBD2 messages, but since some CAN messages are sent over PIDs services these are taken as OBD2 packets, so Flipper can display typical data.
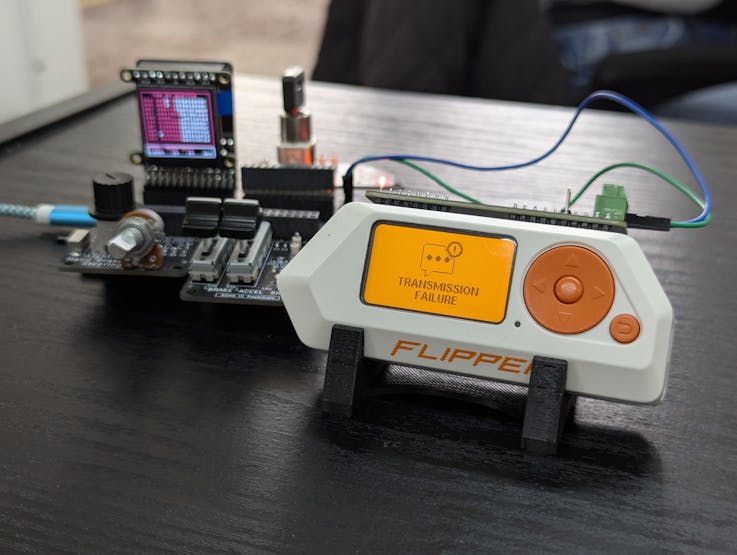
Here are some pictures for more of the tests with RAM:
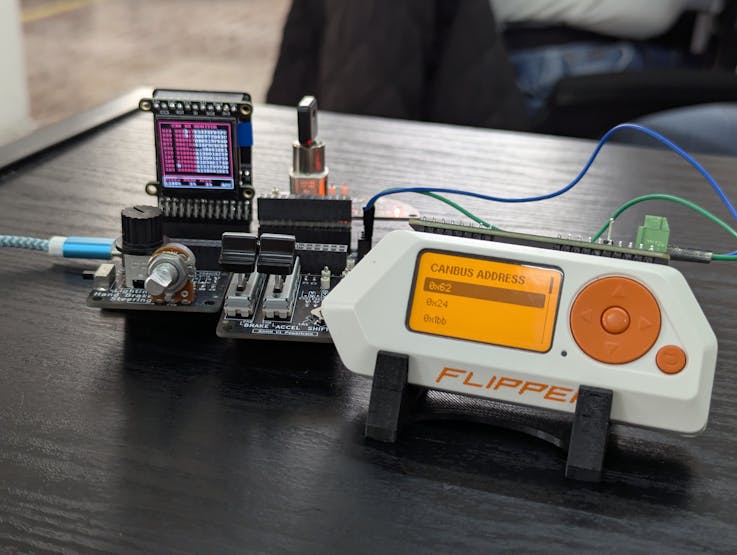

Some data emulation is not supported by RAMN, like the VIN and DTC codes, so it is expected to see an error message.
Concluding
The CAN Bus Add-On and the CAN Bus App for the Flipper Zero are versatile tools that extend their functionality beyond automotive diagnostics into industrial CAN network applications and so on. Paired with the right knowledge and wiring, this setup provides users with a powerful platform to monitor, analyze, and even interact with CAN communication in real-time. Whether you're troubleshooting, experimenting, or learning about CAN bus protocols, this add-on offers a portable and user-friendly solution to dive into the world of Controller Area Networks.
We invite you to visit other tutorials or the CANBUS Add-On Shield documentation to learn more:
Follow us for more projects and updates to come!
'News' 카테고리의 다른 글
| Hacking Subaru: Tracking and Controlling Cars via the STARLINK Admin Panel (펌) (0) | 2025.02.02 |
|---|---|
| Solar Storm supply chain attack (0) | 2020.12.25 |
| twitter iOS News (0) | 2020.12.07 |
| [News] DNS Cache Poisoning (0) | 2020.12.06 |
| 테슬라 모델X 전자 제어 장치 해킹 관련 (0) | 2020.12.06 |












