Information Disclosure via Misconfigured AWS to AWS Bucket Takeover
Hey! Welcome to a new write up on my recent finding of a Misconfigured AWS bucket and how i was able to Take full control of the AWS…
medium.com
Information Disclosure via Misconfigured AWS to AWS Bucket Takeover
Hey! Welcome to a new write up on my recent finding of a Misconfigured AWS bucket and how i was able to Take full control of the AWS bucket.
I was checking out the website mainly for the IDOR Vulnerabilities as those are considered as High priority bugs and are paid in high range. I was trying to check every possible end-points to find any parameter to manipulate the numerical value so i fired up my burp suite and sent the request to spider tab to check out all the endpoints but i failed because they have encrypted every numerical value using salted algorithm.
As it was not possible to find any IDOR , i found an interesting endpoint where i was able to set my organization logo and there was a direct link to the logo which was residing at an AWS bucket. You can check below:
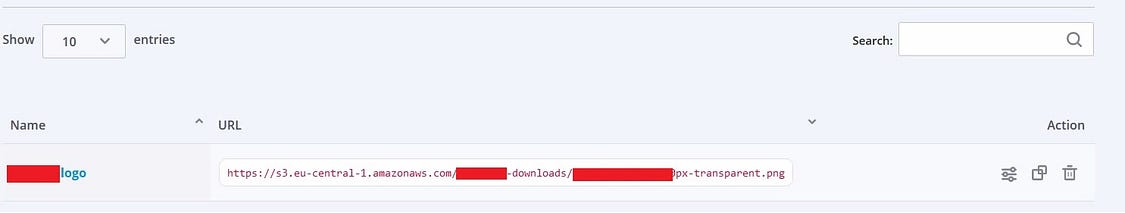
So i checked this logo by directly coping it and opening it in the new tab:

Basically i never though that i will find anything like this so i never thought of doing anything in any programs or private programs i have worked on but that day i thought that let’s go to origin directory of the file[in hacker’s language ../ ;)]. so i checked it by going to the origin directory as you can see:
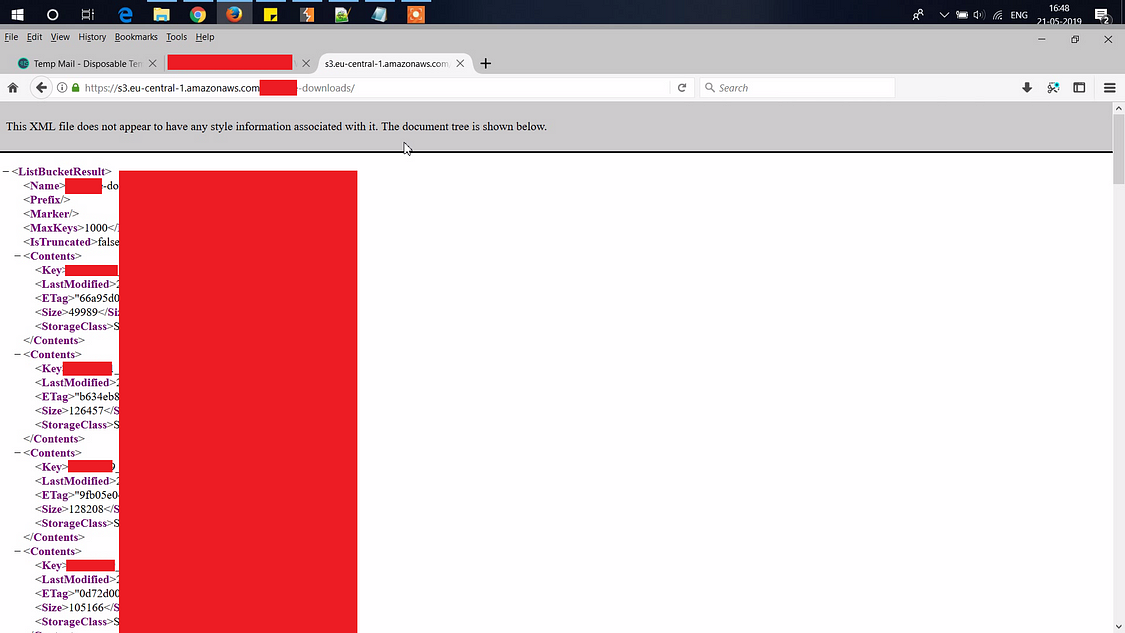
Bingo! this was a proper Information disclosure due to Misconfigured ACL of the AWS bucket. I was happy and thought of reporting this directly but as a Hacker you are always overwhelmed and curious to find all the juicy information that might be possible to exploit. So without wasting any time , I went ahead to check out all the files getting listed in the Directory but before that i tried to access one of the file to check if the files are real or not.
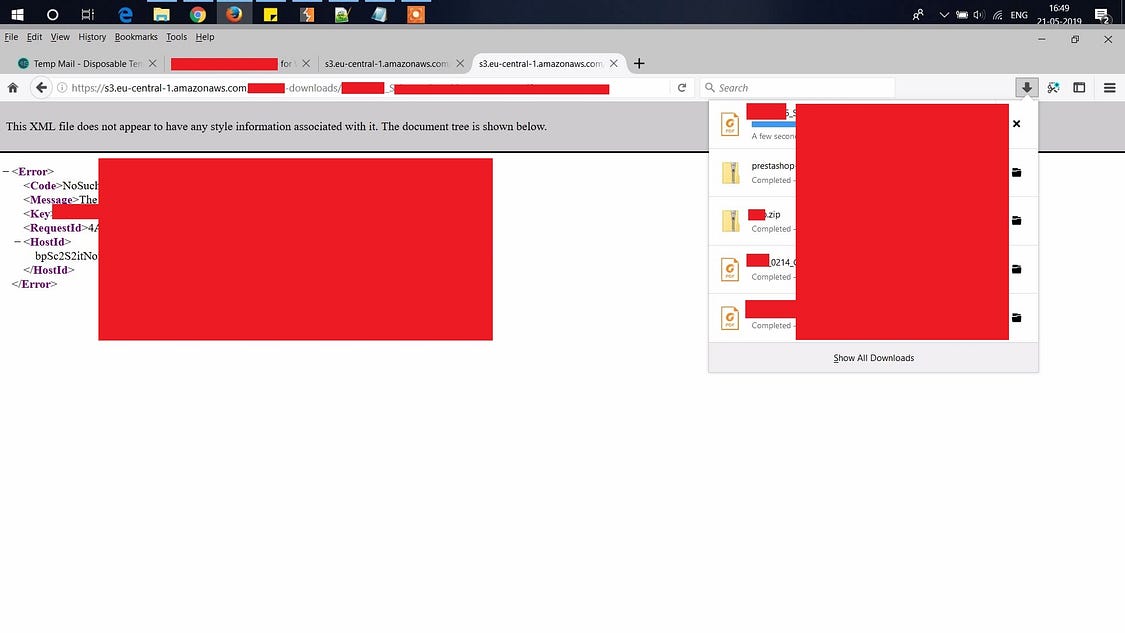
Than i opened the file to see what is the content:
Now i am confident enough that all the files available here are legitimate[Use of sophisticated word to look geeky 🤓] and we can see all the internal files of the xyz company here with small tutorials , screenshot and this was an internal S3 bucket used for training and demonstration purposes, such as sharing screenshots of their products……I guess so now you can see why it’s Critical.
At that moment , I felt like it’s enough to report now but i took a chance and thought if there is something else the bucket is offering to compromise itself…Damn Is it possible? Let’s see what happens…. I started checking files with extensions, especially with .zip or .htm or .eml or .doc or .csv and while searching through the entire bucket[which consisted of more than 700+ files] and found the first zip file:

So i downloaded it and checked the contents:
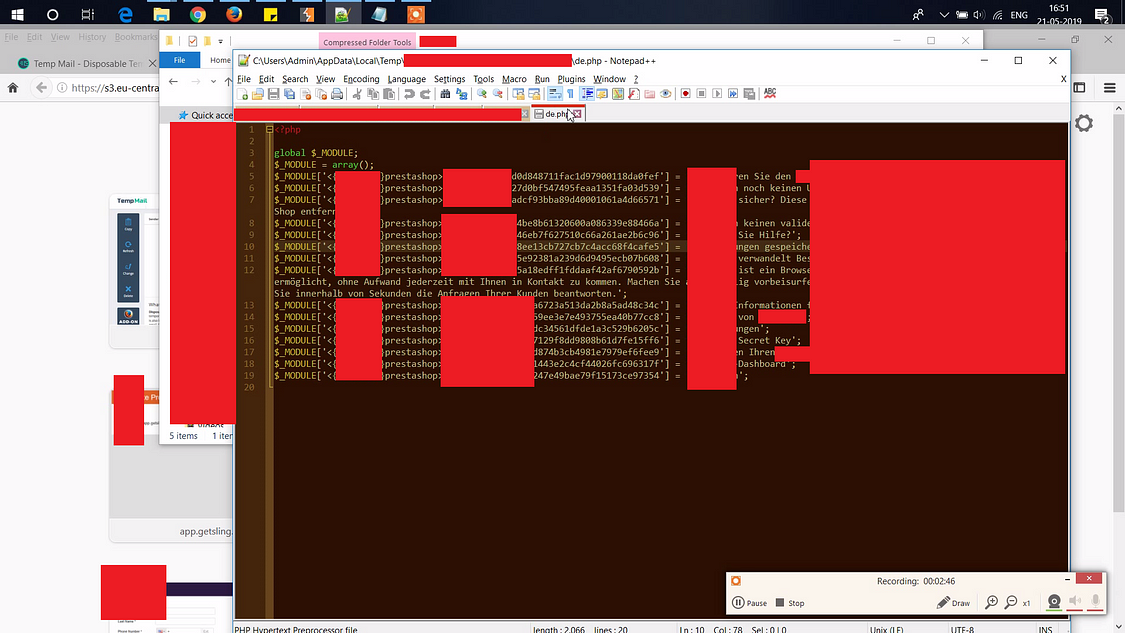
After checking on the files of that zip , i figured out that it’s not going to offer me anything to compromise the AWS bucket. So i started searching for other zip files and found an interesting zip file in the AWS bucket:
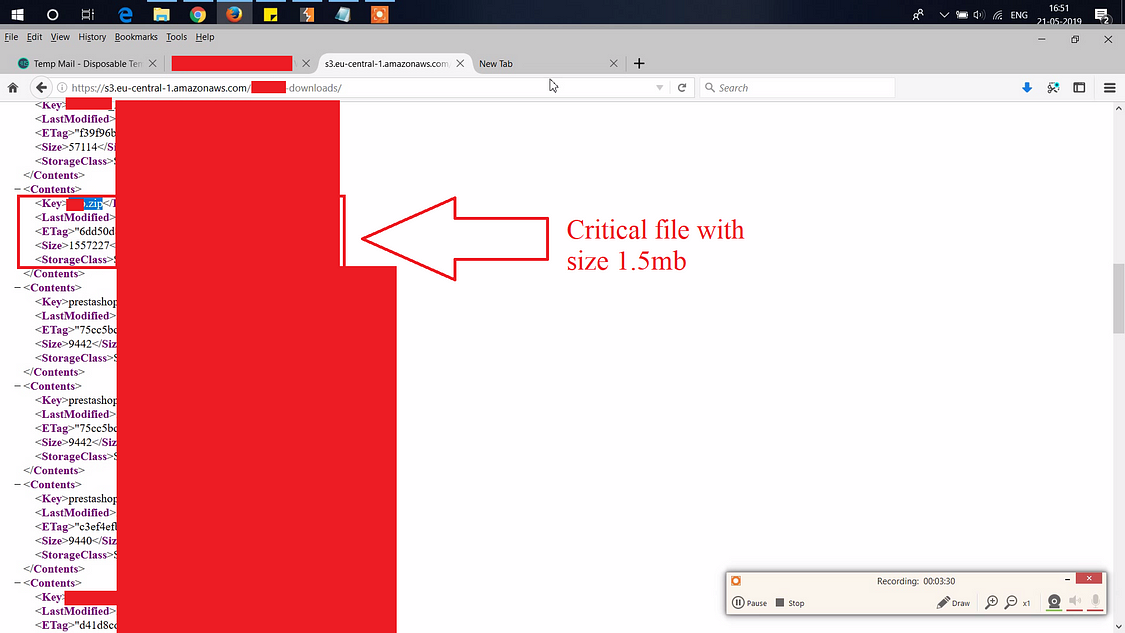
Now i downloaded the file and opened to check the contents:
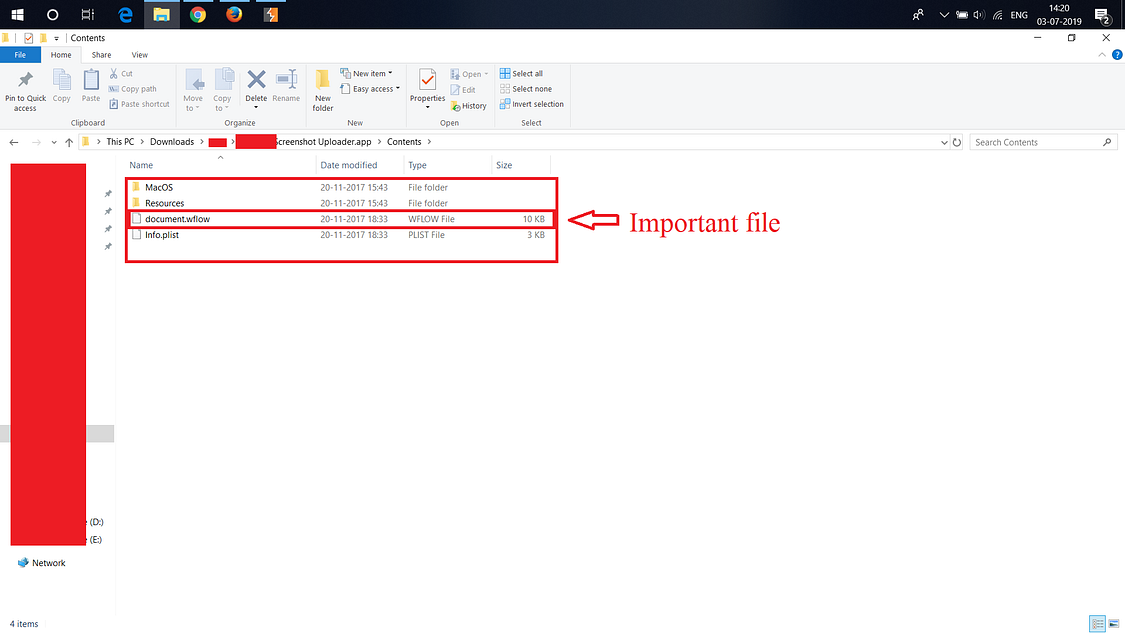
I checked all the files but the important file was the “document.wflow” , It has everything i required to TAKEOVER the AWS Bucket. Let’s check the content:
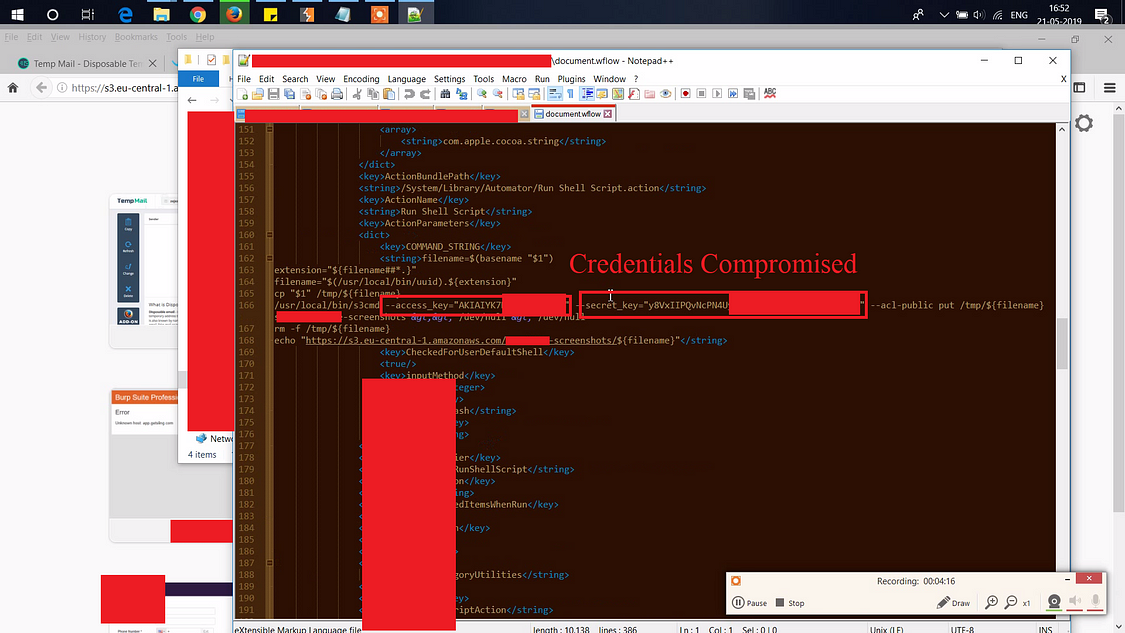
I was so happy to see this credentials but now the funny thing is that i don’t know what to do with that because Zero knowledge in AWS. So the best way i found was i asked one of my office colleague who is a Dev and works on AWS. He told me that , Go to google and download S3 Browser to start browsing the AWS bucket if you have the “access_key” and “secret_key” which was a very new learning experience in the field of my Web Application Penetration Testing. I was like:
So i downloaded it and started providing all the required credentials:
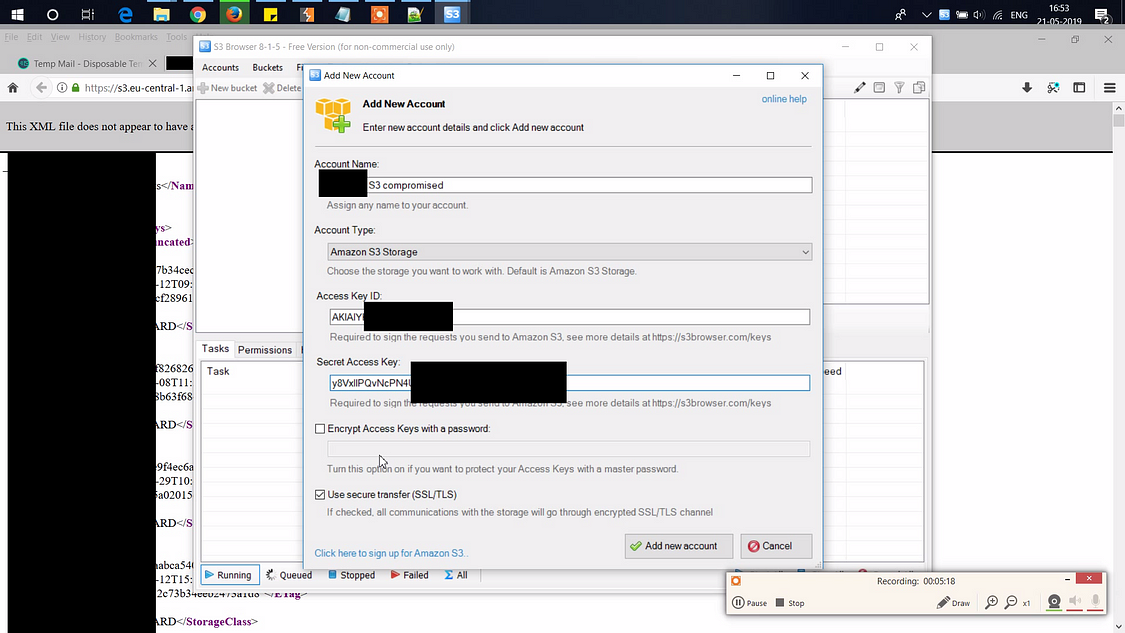
Boom!
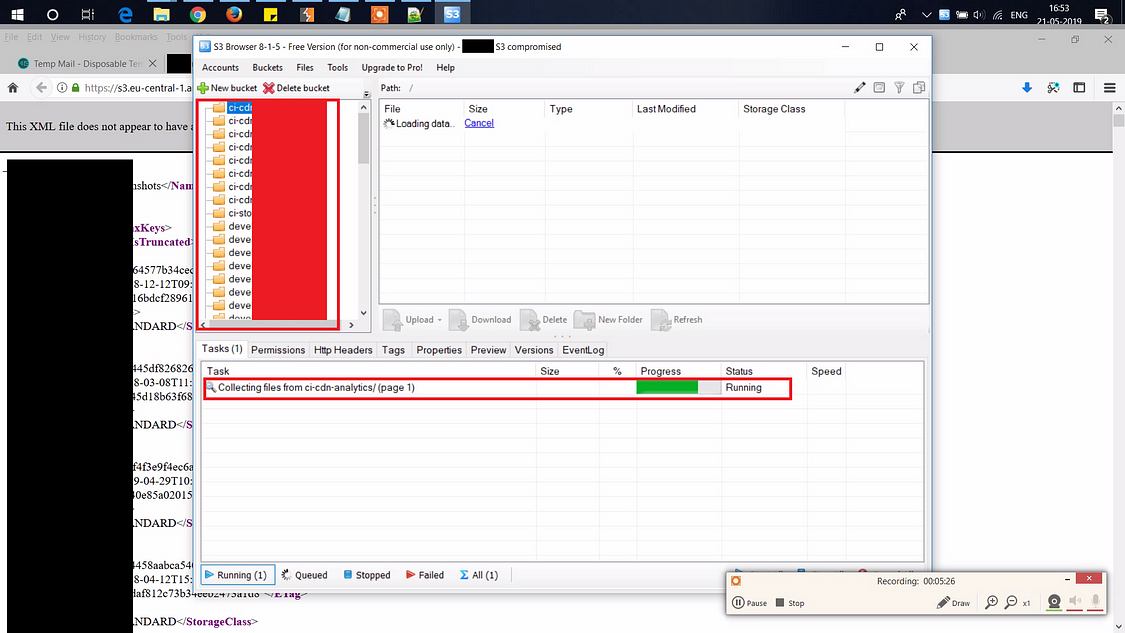
The next thing i checked on the Access Control List permission on each directory and found a directory with full access:

With the full access to this directory now I am the Owner of this and i can upload any file i want , I can delete it and i can Delete the whole directory. I had all the access in the world but As you all know we are all ethical in what we do so to make a Proof Of Concept i uploaded a file:
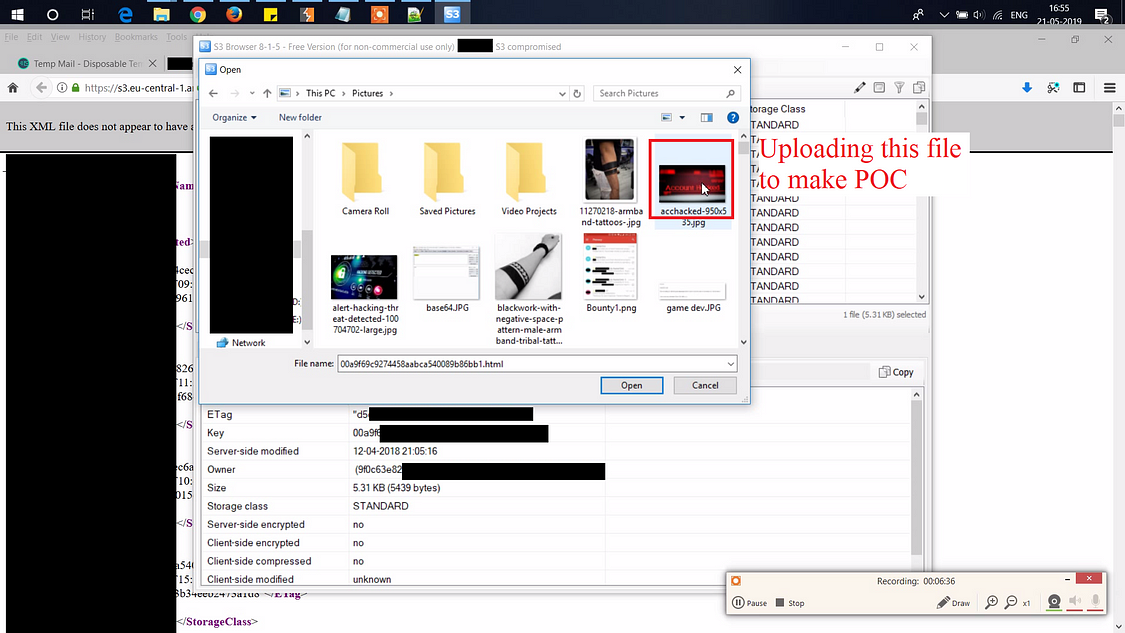
Now to re-verify it I checked it in the public facing bucket with my uploaded file name.
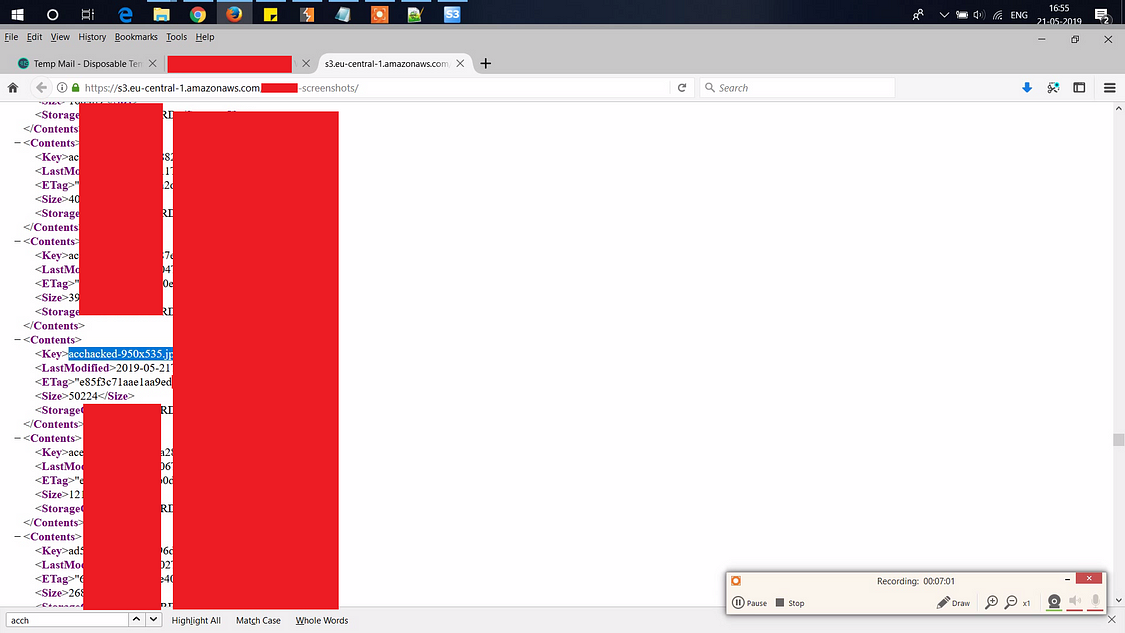
Final check I pasted the filename in the URL and checked:
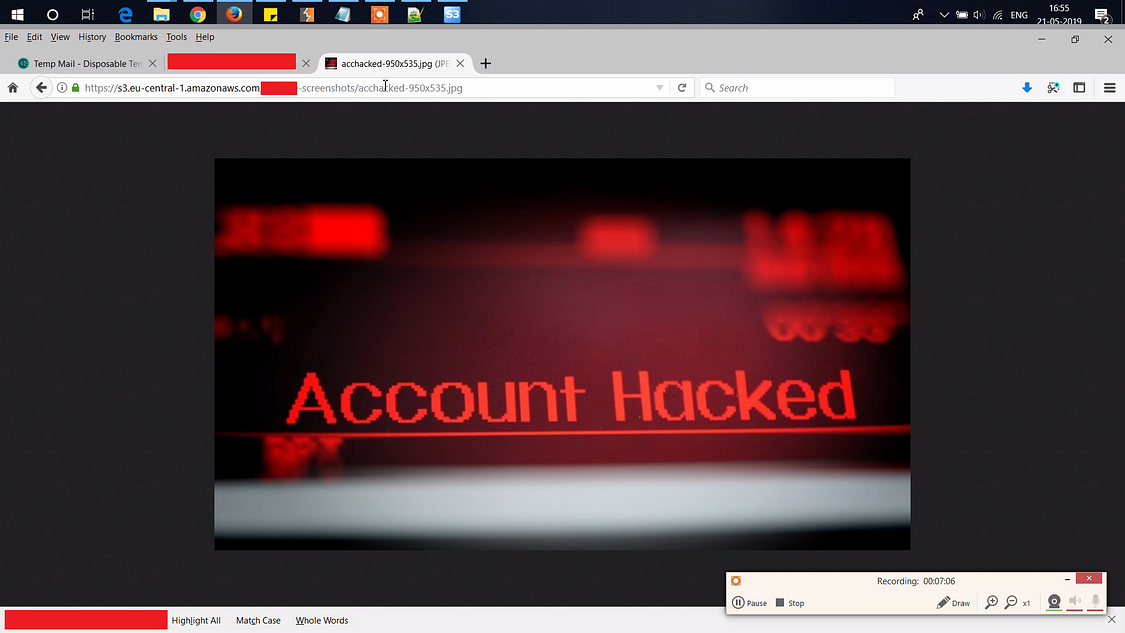
Damn! AWS Bucket Takeover!
Following my initial report and its review, they had promptly and fairly compensated me for letting them know about this bug. I am really thankful for that :)
'경로 및 정보' 카테고리의 다른 글
| Fiddler 셋팅 (0) | 2023.11.10 |
|---|---|
| VDI python Package 설치 (0) | 2023.11.08 |
| Hacking Swagger-UI - from XSS to account takeovers (0) | 2023.11.02 |
| Active Directory 정보 수집 (0) | 2023.10.25 |
| Active Directory Pentesting Resources (1) | 2023.10.25 |



