https://crazykim2.tistory.com/478
[JAVA] Window10의 JAVA SE 11 설치하기
안녕하세요 포스팅이 늦은 것 같지만 이번에 윈도우를 포맷하면서 자바를 다시 설치하게 되었습니다 자바 개발을 처음하거나 자바를 설치한지 오래되어서 기억이 안 나는 분들을 위해 자바 설
crazykim2.tistory.com
'경로 및 정보' 카테고리의 다른 글
| 노트패드 \r\n 개행 (0) | 2022.01.17 |
|---|---|
| nmap script nse 스캐닝 (0) | 2021.12.29 |
| Interact.sh 경로 건 (0) | 2021.12.15 |
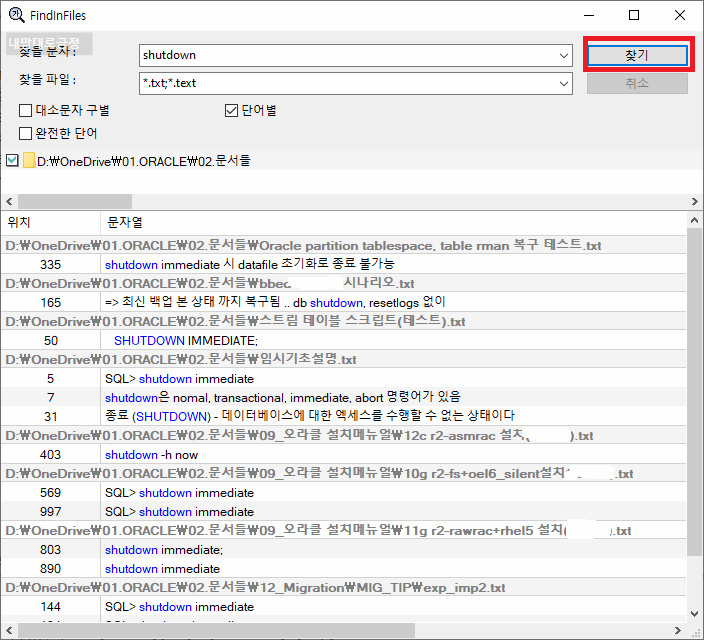
| windows 10 텍스트 검색 경로 (0) | 2021.12.11 |
| window search 기능 활성화 (0) | 2021.12.10 |